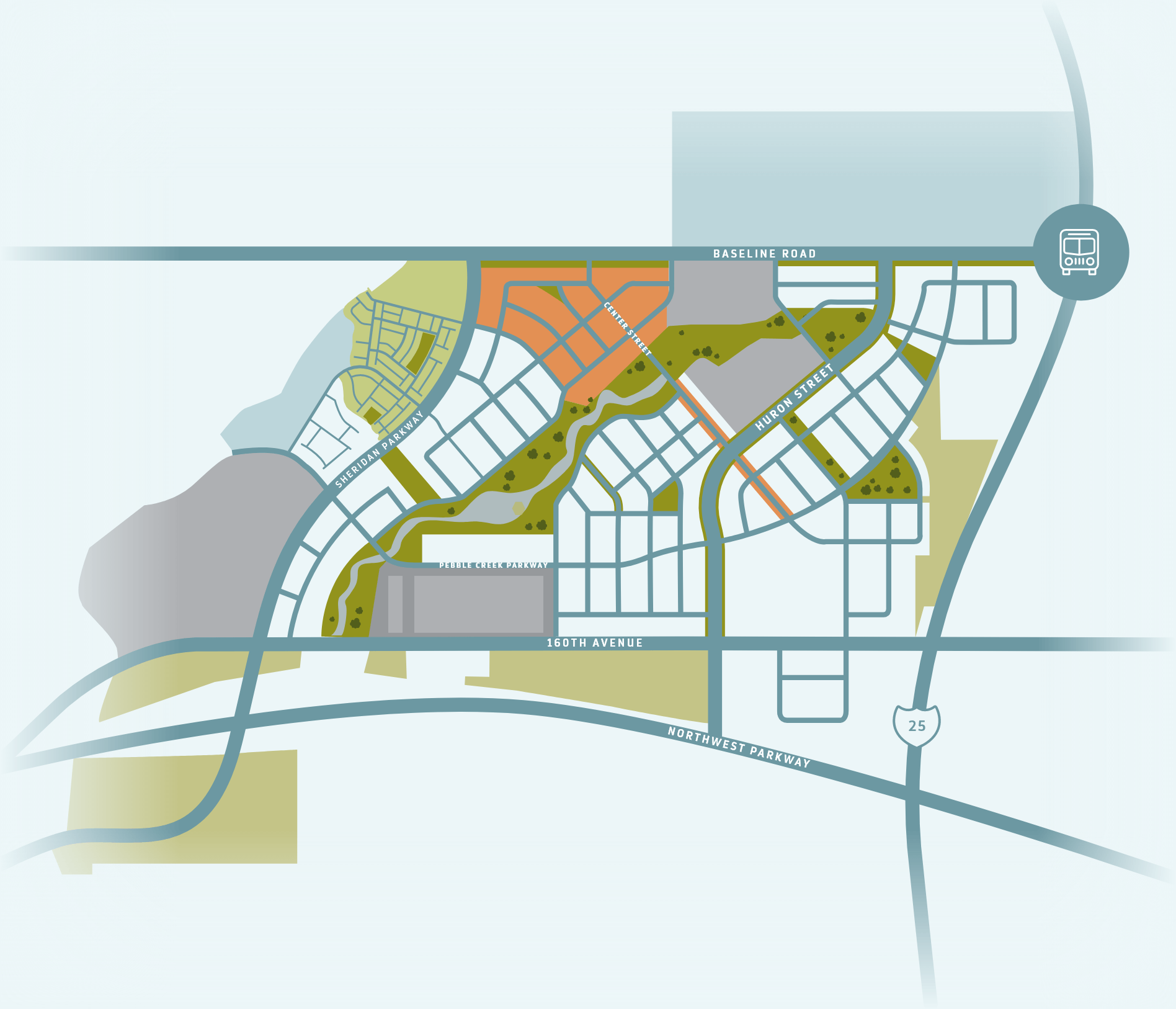
Intro
An iPhone user’s worst nightmare is to have someone gain persistent control over his/her unit, such as the power to record and get a grip on all task without also having to be in identical room. In this website post, we present a vulnerability that is new “Trustjacking”, makes it possible for an assailant to accomplish exactly that.
This vulnerability exploits a feature that is ios iTunes Wi-Fi sync, that allows a person to handle their iOS device without physically connecting it for their computer. a tap that is single the iOS unit owner as soon as the two are linked to the same system enables an assailant to achieve permanent control of the unit. In addition, we’re going to walk through past relevant weaknesses and show the changes that Apple has manufactured in purchase to mitigate them, and just why they are not adequate to stop comparable assaults.
A recap of relevant past vulnerabilities / assaults
We saw a few magazines in the past that discuss leveraging unauthorized USB connections to get information that is private cellular devices.
Prior to iOS 7, linking an ios unit to a brand new computer did not require any authorization through the unit owner. Juice jacking [1] [2] [3] uses this behavior and it is in a position to take sensitive and painful information from products and might install spyware regarding the victim’s unit. Apple solved this problem by the addition of the popup asking for the consumer to authorize brand new computers before enabling any sync operations.
Another publication talks about Videojacking, which uses the capability of Apple’s connector to be utilized as an HDMI connection to get a screen recording of iOS devices while attached to a charger that is malicious.
Both exploits permitted an assailant possible usage of delicate information, however their major limitation had been that all things are feasible just although the device is physically linked to the malicious equipment – disconnecting these devices prevents the assault movement.
Trustjacking enables an assailant to gain a more constant and persistent your hands on the product and wthhold the same abilities long after the unit was disconnected from the malicious equipment. To comprehend how this ongoing works, we first need certainly to explain iTunes Wi-Fi sync.
What exactly is iTunes Wi-Fi sync?
iTunes Wi-Fi sync is a tremendously useful function that permits iOS devices become synced with iTunes and never have to physically link the iOS unit into the computer.
Enabling this feature requires syncing the iOS unit with iTunes first by linking to a computer with a cable, then allowing the possibility to sync aided by the iOS unit over Wi-Fi.
Trustjacking – so how exactly does it work?
Upon connecting an iOS device to a different computer, the users are increasingly being expected if they trust the connected computer or perhaps not. Deciding to trust it is allowed by the computer to keep in touch with the iOS unit via the conventional iTunes APIs.
This enables the pc to gain access to the pictures regarding the unit, perform backup, install applications and many other things, without requiring another verification through the individual and with no noticeable indicator. Additionally, this enables activating the “iTunes Wi-Fi sync” feature, that makes it feasible to carry on this type of interaction utilizing the device even after it is disconnected from the computer, so long as the pc together with iOS unit are connected to the same network. It is interesting to notice that allowing “iTunes Wi-Fi sync” will not require the victim’s approval and that can be carried out purely through the computer part.
Obtaining a real time blast of the device’s display screen can be carried out easily by over and over seeking screenshots and showing or recording them remotely.
It is critical to observe that apart from the first solitary point of failure, authorizing the harmful computer, there isn’t any other system that prevents this access that is continued. In addition, there’s nothing that notifies the users that by authorizing the computer they enable use of their device even with disconnecting the USB cable.
Demonstration
Imagine listed here situation: a target links their phone to a totally free charger in a airport; upon linking his phone to your charger a popup message seems in their device, asking for him to accept the connected unit. Approving this demand may appear reasonable: the victim would like to charge their device, the ongoing solution seems legitimate also it seems that absolutely nothing suspicious occurs after the approval.
Attack Flow
Through the individual viewpoint, all he previously to accomplish is link his unit up to a malicious charger / computer (may also be their own computer, as outlined in the future) and select to trust it.
Reading the writing, the consumer is led to think that this might be just appropriate whilst the unit is actually attached to the computer, therefore assumes that disconnecting it will probably avoid any use of their data that are private https://besthookupwebsites.net/escort/davie/. Even though these devices is connected for an extremely period that is short of, it really is enough for an attacker to perform the steps needed to steadfastly keep up visibility of most actions done from the unit after it really is disconnected.
The attacker has to just just take two actions:
- Permit the unit to get in touch to iTunes
- Enable iTunes Wi-Fi sync
These actions may be automatic by harmful computer software. They interestingly don’t require any approval that is additional the target and do not trigger any indicator regarding the unit that one thing is going on. As soon as these actions are finished, the product doesn’t have become actually attached to the attacking hardware anymore. Now the attacker can get a handle on the product remotely, so long as the target and attacker are connected to the network that is same.
To be in a position to see the target’s device screen, the attacker has to install the developer image suited to the target’s device iOS version; then, they can simply take screenshots repeatedly and see the product’s screen in near real time. Installing the developer image are carried out over Wi-Fi and will not need regaining real usage of the product. The hacker has continued access and can reinstall it easily although a restart may remove the developer image from the device.